When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
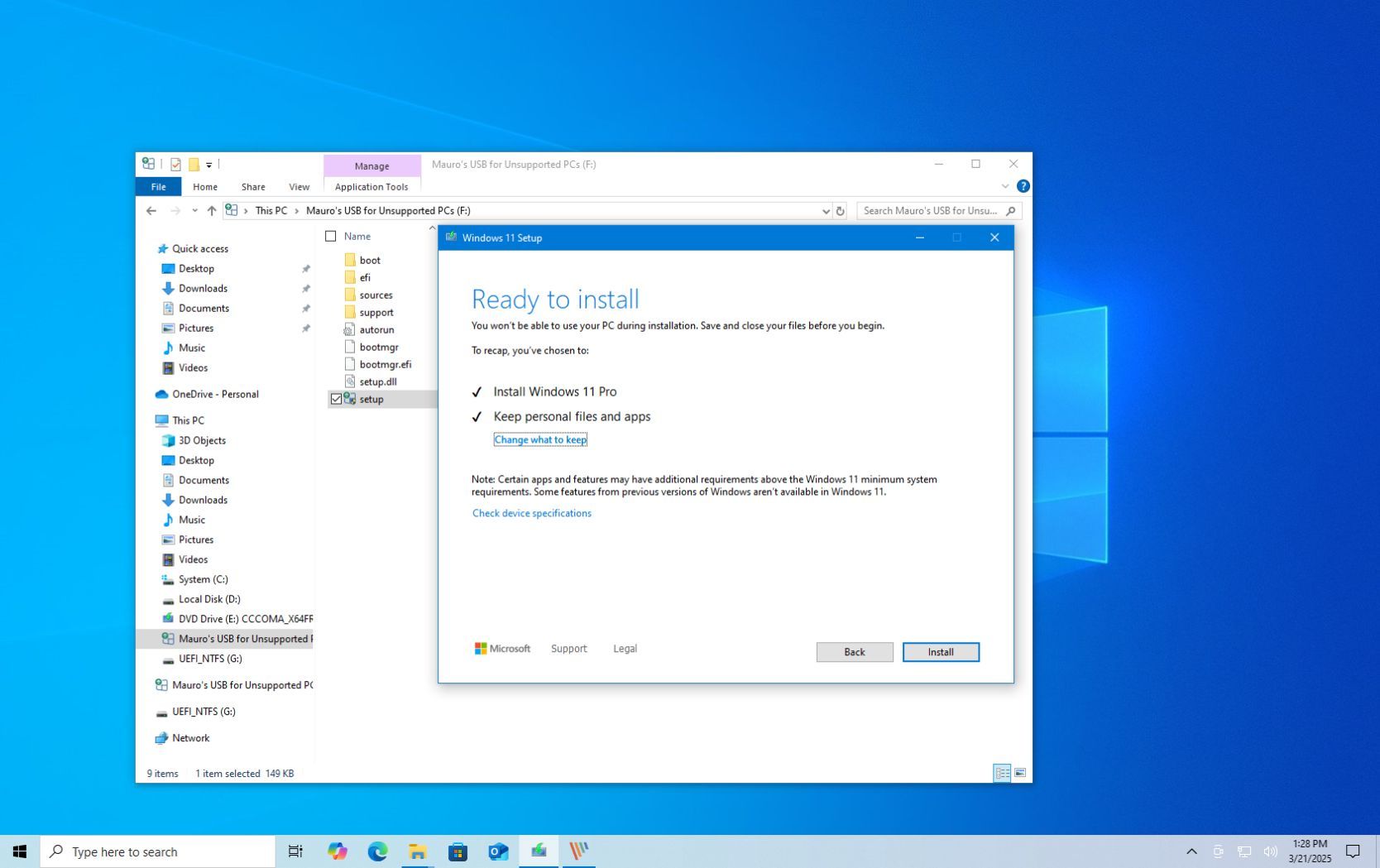
User reluctance to upgrade to Windows 11 can partly be attributed toMicrosoft’s stringent operating system requirements.
These requirements limit the operating system’saccessibility to unsupported hardware missing salient features like Secure Boot and TPM.

Microsoft finally patched the security threat (CVE-2024-7344), allowing bad actors to gain unauthorized access to Windows 11.
However,Microsoft finally patched the security threatearlier this week.
As you may know, Secure Boot is one of the stringent system requirements for running Windows 11.
The security feature prevents malicious firmware from running when a equipment is booting.

Moreover, it makes the malware less susceptible to defense mechanisms that ship with the operating system.
The researcher noticed that a digitally signed app bypassedMicrosoft’s strict manual review process for third-party UEFI apps.
The researcher further disclosed that the app was buried under an XOR-encoded UEFI app called reloader.efi.
The manual review process leverages UEFI’s LoadImage and StartImage for the Secure Boot process.
Perhaps more concerning, reloader.efi wasn’t unique to Howyar Technologies' system recovery software.